Mining With SQLs
RDP, NSSM, Install.bat, Update.bat, Mining Done
https://thedfirreport.com/2020/04/20/sqlserver-or-the-miner-in-the-basement/
This write up from the DFIR Report went through a relatively simple piece of malware that was installed on one of their honeypot servers. It was a good example of an easily preventable malware issue that could simply occur due to misconfiguration.
We stepped through the article and tried a lot of what was within the scripts to test our monitoring ruleset for a Windows server. Below is what worked and didn’t work as we went through this process.
Initial Access
Initial access was from a pair of IP addresses which had nothing to speak of in terms of IP threat intelligence or reputation but did seem to be located in areas which would probably be abnormal for Australian organisations.
95.156.252.94
ISP: Pars Online PJS
Reverse DNS: 95.156.252.94.pol.ir
Country: Iran
Is TOR Node?: False
Shodan Information
Hostname(s): 95.156.252.94.pol.ir
Tags: self-signed, database
185.155.96.83
ISP: Ou Web Hosting Solutions
Reverse DNS: N/A
Country: Estonia
Is TOR Node?: False
Shodan Information
Hostname(s): N/A
Tags: N/A
For the initial access we will assume, as it is not included in the writeup, that the account used had an easily guessable password without brute forcing lockout protection. In this case being able to perform an IP reputation check is of little value unless we have some logs with high quality data points within. A set of common logs that would be relevant in this case and their value to security monitoring is shown below.
| Name | Description | Outcome |
|---|---|---|
| Server Authentication Logs | Endpoint authentication logs on externally accessible services where the username, authentication result and source IP are included will provide the best visibility. | High Confidence Alarm |
| Firewall Logs | Host Based/Perimeter firewall logs without any context of the actions performed after a permit or deny provide little value and based on the amount of scanning activity generated against public facing services may produce alarms in quantities too large to effectively investigate. This is especially true if there are perimeter firewall rules allowing public access to infrastructure on common access protocols such as SSH or RDP. | Low Confidence Alarm |
| Load Balancer Logs | If an organisation has deployed Load Balancer technology that is responsible for authenticating users to services then this can be a valuable log source. Most modern load balancers have detailed logs and can even include Web Application Firewall type logs from the same device. If a load balancer authentication module includes username, authentication result, source IP and the destination service it will provide the ability for high confidence detections to occur. | High Confidence Alarm |
In this case having authentication logs for the RDP login would have shown there were logins to a server from Estonia and Iran. This would likely have resulted in an alarm worth looking further into. If firewall logs were the only logs available then it’s likely this access would be part of the general internet noise and not investigated.
Install.bat
The article then details the contents of an install script that was executed on the server. We have modified the actual commands, as there were typoes and commands that simply would not run on our test server. We only used a single example of each type. As always run these types of commands in dedicated test environment, as a lot of them while not malicious on their own may alter the system state.
@echo off
net stop TrustedDriver
echo,Y|icacls c:\windows\fonts\*.exe /T /Q /C /RESET
wmic process where ExecutablePath='c:\\windows\\Fonts\\svchost.exe' delete
del /q /f "c:\test"
attrib +s +h "c:\Windows\Fonts\svchost.exe"
taskkill /f /im wscipt.exe
Some of the interesting commands are explained below;
- icacls - Used to show of modify Access Control Lists (ACLs) within Windows. In this case the command is setting all of the “.exe” files in fonts directory to the default inherited ACLs with the “/RESET” parameter.
- wmic - Provides a command line interface for the Windows Management Instrumentation (WMI) which allows for a huge range of management tasks to be performed within Windows. In this case it is being used to kill a process that matches the ‘where’ clause. It's an interesting use of WMIC.
- attrib - This command changes attributes. The use of ‘+h’ sets the file to hidden to hide it.
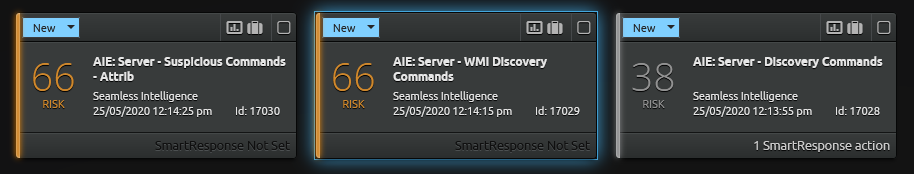
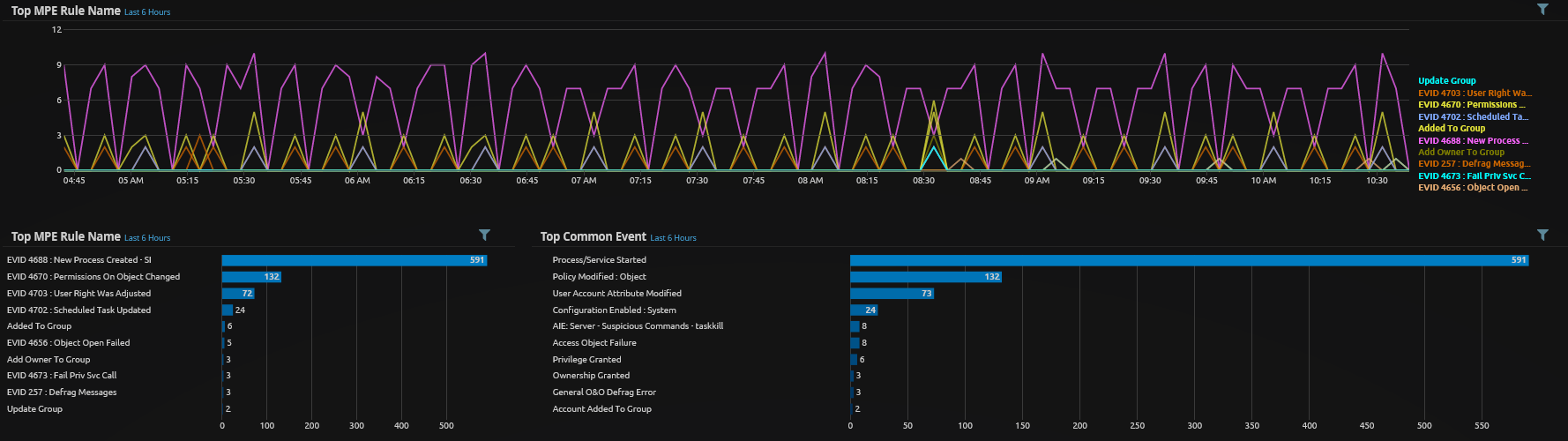
From this set of commands we can begin testing and altering or building new rules to capture some of the more suspicious activity. As can be seen above we have tested a few types of rules with varying degrees of success, the most difficult part of these types of activities is they often do not look radically different than some normal administrative tasks. There are two ways we create rules around these types of activities;
- Generic Rules - The above rule titles “Server – Discovery Commands” is an example of a generic rule where a number of discovery type commands are bunched into the rule. These rules are generally quite low confidence and we often auto close them after adding certain elements to rules for further monitoring.
- Specific Rules - For discovery commands and techniques where we can apply some more logic a specific rule may be created. In these rules we would look for the additional indicators that mark the event as different from a normal administrative action. For example in the “Server – Suspicious Command – Attrib” rule we need the “+h” parameter to be set for the rule to fire.
Ultimately there is a fine line between reducing false positives and removing the ability to detect something. In the case of the DFIR writeup the malware performs so many actions on such a short time frame it is hard to miss.
Registry
Next there are some components installed, one of which changes the registry to maintain persistence. Monitoring specific parts of the Windows registry is gold and Sysmon is by far the easiest freely available way to do it. Below shows the addition to the registry which gets part of the malware to run every time any executable is run.
Registry key: HKLM\SOFTWARE\Classes\exefile\shell\open\command
Value: %SystemRoot%\svchost.com “%1” %*
Below is the command to add a key to the registry which will test your monitoring.
reg add HKLM\SOFTWARE\Classes\exefile\shell\open\command /v %SystemRoot%\hacker.com /t REG_SZ /d "“%1” %*"
Below is the Sysmon config related to this area of the registry. Once again you can create a rule to look for any Sysmon events related to the registry or have rules for each specific item you are looking for. It’s interesting how many things write stuff to the ‘run’ area for execution on startup for example, alerting on every one of those would be a waste of time.
!--SYSMON EVENT ID 12 & 13 & 14 : REGISTRY MODIFICATION [RegistryEvent]--!
RegistryEvent onmatch="include"
TargetObject condition="contains">shell\open\command\ /TargetObject
Update.bat
Next is update.bat which updates some stuff and performs a few activities related to scheduled tasks and service stopping & starting. All the other commands are variants of things seen in the install.bat section.
net stop TrustedDriver
taskkill /f /im wscipt.exe
SCHTASKS /Delete /TN /SERVERQR /F&SCHTASKS /create /tn /SERVERQR /sc DAILY /mo 365 /tr "cmd /c echo,Y|calcs c:\windows\fonts*.exe /G everyone:f"
Some of the interesting commands are explained below;
- net - There are many 'net' commands and monitoring them selectively is preferable to a generic ‘net’ rule. In this instance the malware is using the ‘net’ command to stop and start Windows services which is a common event on Windows Servers.
- taskkill - Kills a task. Fairly uncommon to see an admin use this on the command line.
- schtasks - Creating and deleting scheduled tasks is common and will vary in every environment. The most important part of the task is what is being executed which in this case is an ACL change on an executable file. In this case rules looking for weird activity within the command are the way to go but try not to be too specific due to trying to specifically detect an example.
No Logs
There are some commands that are run which produce no "Process Creation" logs within Windows such as "del" and echo'ing content into a file. This is actually quite a big topic and we'll be creating a separate write up on these commands.
del /q /f "c:\test"
echo 127.0.0.1 seamlessintelligence.com.au>> %WINDIR%\system32\drivers\etc\hosts
start %windir%\fonts\hackerman.exe
Sqlserver, or the Miner in the Basement - Original Articlehttps://thedfirreport.com/2020/04/20/sqlserver-or-the-miner-in-the-basement/
A great writeup by The DFIR Report with the inclusion of script commands and other IOCs.